|
Database settings - Encryption |



|



|
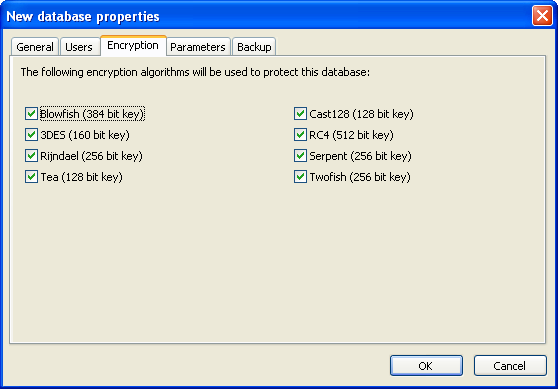
Select which encryption algorithms will be used to protect the database at this property page. See Additional information topic to learn how the database is encrypted.
![]() Blowfish - one of the most powerful block encryption algorithms, developed by cryptography guru Bruce Schneier. Block size is 64 bits, key size - up to 448 bits;
Blowfish - one of the most powerful block encryption algorithms, developed by cryptography guru Bruce Schneier. Block size is 64 bits, key size - up to 448 bits;
![]() 3DES - uses DES algorithm, by is applied three times with different keys, which increases dependability when compared to DES but does not change the situation radically (still vulnerable);
3DES - uses DES algorithm, by is applied three times with different keys, which increases dependability when compared to DES but does not change the situation radically (still vulnerable);
![]() Rijndael - algorithm, developed by Joan Daemen and Vincent Rijmen. Meets AES standards (Advanced Encryption Standard). Uses blocks of different sizes (128, 192 and 256 bits) and equal-size keys;
Rijndael - algorithm, developed by Joan Daemen and Vincent Rijmen. Meets AES standards (Advanced Encryption Standard). Uses blocks of different sizes (128, 192 and 256 bits) and equal-size keys;
![]() Tea - strong algorithm (Tiny Encryption Algorithm). Its most prominent feature is a very small size. Tea is very simple, does not use table values and is optimized for 32-bit processor architecture, which makes it possible to use it with ASSEMBLER, even when the code size is extremely small. The drawbacks include slow work and the need for "data scrambling" since no tables are used;
Tea - strong algorithm (Tiny Encryption Algorithm). Its most prominent feature is a very small size. Tea is very simple, does not use table values and is optimized for 32-bit processor architecture, which makes it possible to use it with ASSEMBLER, even when the code size is extremely small. The drawbacks include slow work and the need for "data scrambling" since no tables are used;
![]() CAST128 - a rather dependable algorithm with key length up to 128 bits. Developed by C.M. Adams and S.E. Tavares, who offered it at AES competition;
CAST128 - a rather dependable algorithm with key length up to 128 bits. Developed by C.M. Adams and S.E. Tavares, who offered it at AES competition;
![]() RC4 - a stream encryption algorithm used in many network security systems (for example SSL protocol used in Netscape and Windows NT password encryption). The major advantages of this code is very fast speed and adjustable key size. This algorithm was developed in RSA by Ronald Rivest. RC stands for "Ron's Code" or "Rivest Cipher". Used to be the intellectual property of RSA up to 1995;
RC4 - a stream encryption algorithm used in many network security systems (for example SSL protocol used in Netscape and Windows NT password encryption). The major advantages of this code is very fast speed and adjustable key size. This algorithm was developed in RSA by Ronald Rivest. RC stands for "Ron's Code" or "Rivest Cipher". Used to be the intellectual property of RSA up to 1995;
![]() Serpent - developed by Lars Ramkilde Knudsen, a famous cryptographer and cryptoanalyst, known for successful cryptoattacks of several popular codes, who worked and lectured in Norwegian, Swedish, and Belgian universities. Currently, Lars is a professor of math at Denmark's Technical University;
Serpent - developed by Lars Ramkilde Knudsen, a famous cryptographer and cryptoanalyst, known for successful cryptoattacks of several popular codes, who worked and lectured in Norwegian, Swedish, and Belgian universities. Currently, Lars is a professor of math at Denmark's Technical University;
![]() Twofish - algorithm that replaced Blowfish, authored by Bruce Schneier as its predecessor. Considered to be hack-proof (no known incidents of code-cracking).
Twofish - algorithm that replaced Blowfish, authored by Bruce Schneier as its predecessor. Considered to be hack-proof (no known incidents of code-cracking).